Protect Data Against WannaCrypt Ransomware Attacks
The International WannaCrypt or WannaCry Cyberattack launched on May 12, 2017 and affected companies and individual systems in over 150 countries. The 2nd version of this ransomware was released Monday Morning, May 15, 2017. This morphed variation of a ransomware virus is unique in that it also executed massive scans on other vulnerable machines used within the same network and it just spread like a wildfire. Users running on supported Microsoft Server and Desktop Operating Systems with the latest Microsoft Updates (MS17-010) had a security patch that those using Windows XP, Windows Vista and Windows Server 2003/2008 unfortunately did not. The virus would double the ransom from $300 -$600 if it was unpaid within 3 days. Hospitals, Medical Facilities, Shipping companies, Financial Institutions and so much more were affected on an international level. So now what? How can you stay protected against the WannaCrypt Virus and it’s variants?
Our first word of advice: If you are using a computer that is running on Windows XP or Vista, please just stop everything and either upgrade or purchase a new computer before you are the next victim. Unless, you don’t care about any of your files or data… If you are working in a company running Windows Server 2003, Windows Server 2000, Windows Server 2008, please note that the party is over and it’s time to think about a new solution that will protect your company data, as well as money lost when these cybercriminals attack again and I am telling you now, that you will be a target over and over again until you move to a newer Desktop and Server Operating System that can enable protective factors against this malicious code. These threats are not going to go away.
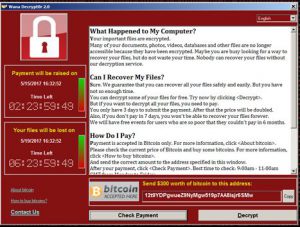
So I ask you here today, what is more important? Spending thousands on an emergency mission critical IT expense or the comfort in knowing that your planned technology investment will protect your invaluable data and keep your company working while perhaps your competition might be left dead in the water? Do you place more value on not investing in your own security which inevitably will be attacked, or do you strive to preserve productivity and the integrity of your proprietary company data? If you do nothing, be prepared to be hit with intrusions such as this:
Obviously most users will want to remove any possibility of this red screen and others like it from taking up valuable time and money. There are a few simple fixes you can implement if you want to protect yourself and your data from this WannaCrypt attack and similar viruses in the future for desktop users and companies using servers:
DESKTOP USERS
- Update Your System Operating System to Windows 7,8 or 10.
- If your system is too old to support an upgrade, please back up your files and purchase a new system. Our staff can help you with that.
- If you are using Windows 7-10, please update your Windows Defender Program
- Install the latest Windows Updates for your Operating System.
SERVERS RUNNING ON WINDOWS SERVER 2003 & SERVER 2008:
- Consider an immediate Upgrade to Server 2008R2 or newer if you want to continue to have a physical hardware solution on premise.
- Consider moving to a Cloud Solution which will automatically run system back ups for you daily.
- Verify and obtain a current backup of all your company data.
BUSINESSES RUNNING WINDOWS SERVER 2008R2 or NEWER:
- If you have been on the fence about using a better router, this is the time to add that extra layer of protection
- Best Practices with routers includes customized security and content filtering features.
- Schedule a network security assessment with Orange County Computer and establish a corrective action plan to safeguard your network.
Remember that once a single computer in your organization is hit by the WannaCry ransomware, the virus looks for other vulnerable computers and infects them as well.
Contact the security experts at Orange County Computer for more information on how to safeguard your network and valuable information at (949) 522-7709 or contact us here.